Heartbeat Encryption - Literally
Source: news.softpedia.com
Received from Robert S.
Researchers from the Chinese University of Hong Kong have developed a solution for securing wireless communication between the modern medical implants and maintenance/monitoring devices. The solution encrypts the communication using a 64-bit key, which is generated by using each patient's heartbeat.
Modern medical implants significantly reduce the need for follow-up surgical interventions. Many such implants are used to regulate vital functions, and can be monitored, updated or controlled remotely via a wireless connection. Regardless of how weird it might sound, hacking such implants is theoretically possible since their connection is just as vulnerable as the connection between other wireless devices.
Obviously, such scenarios could have fatal consequences if we're talking, for example, about pacemakers. Therefore, using reliable encryption algorithms in order to secure communication with such devices makes sense. According to the researchers, the heartbeat-based encryption is not easy to crack because of the constantly changing nature of the heartbeat, which makes it impossible to replicate by using an older record.
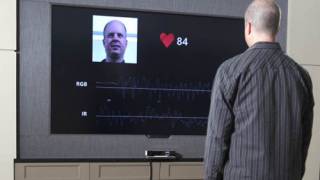
The heartbeat is measured using a person's pulse but, as Carmen Poon, one of the researchers involved in the development of this technology, explains, there are natural minor fluctuations in the Interpulse Interval (IPI). This is irrelevant during a medical intervention because the technology works by taking two measurements in real time, but secures it from hacking attempts using previously registered records.
One measurement is taken by the implant itself and one is taken at the same time from the patient's index finger. The interval between 16 successive heartbeats is used to generate a calibrated 64-bit key. Successful communication between the implants and the external devices is possible only when the keys generated using the two measurements match to a great degree.
During their tests, the researchers used an ECG and a PPG to analyze the data; the registered error rate was of 6.5, which they note is close to the 4.2 error rate of biometric systems like fingerprint recognition. According to Poon, this makes it accurate enough to reject false keys, but flexible enough to account for measurement variations at different points on the body.
Article from: http://news.softpedia.com/news/
Heartbeat-Encryption-Literally-93081.shtml