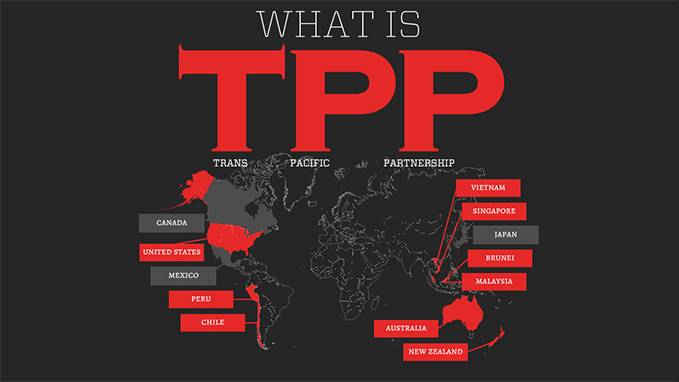
The Final Leaked "Secret" TPP Text is All That We Feared. Top Down Control of the Internet
Source: globalresearch.ca
Since we now have the agreed text, we’ll be including some paragraph references that you can cross-reference for yourself—but be aware that some of them contain placeholders like “x” that may change in the cleaned-up text.
Also, our analysis here is limited to the copyright and Internet-related provisions of the chapter, but analyses of the impacts of other parts of the chapter have been published by Wikileaks and others.
Binding Rules for Rightsholders, Soft Guidelines for Users
If you skim the chapter without knowing what you’re looking for, it may come across as being quite balanced, including references to the need for IP rules to further the “mutual advantage of producers and users” (QQ.A.X), to “facilitate the diffusion of information” (QQ.A.Z), and recognizing the “importance of a rich and accessible public domain” (QQ.B.x). But that’s how it’s meant to look, and taking this at face value would be a big mistake.
If you dig deeper, you’ll notice that all of the provisions that recognize the rights of the public are non-binding, whereas almost everything that benefits rightsholders is binding. That paragraph on the public domain, for example, used to be much stronger in the first leaked draft, with specific obligations to identify, preserve and promote access to public domain material. All of that has now been lost in favor of a feeble, feel-good platitude that imposes no concrete obligations on the TPP parties whatsoever.
Another, and perhaps the most egregious example of this bias against users is the important provision on limitations and exceptions to copyright (QQ.G.17). In a pitifully ineffectual nod towards users, it suggests that parties “endeavor to achieve an appropriate balance in its copyright and related rights system,” but imposes no hard obligations for them to do so, nor even offers U.S.-style fair use as a template that they might follow. The fact that even big tech was ultimately unable to move the USTR on this issue speaks volumes about how utterly captured by Hollywood the agency is.
Expansion of Copyright Terms
Perhaps the biggest overall defeat for users is the extension of the copyright term to life plus 70 years (QQ.G.6), despite a broad consensus that this makes no economic sense, and simply amounts to a transfer of wealth from users to large, rights-holding corporations. The extension will make life more difficult for libraries and archives, for journalists, and for ordinary users seeking to make use of works from long-dead authors that rightfully belong in the public domain.
Could it have been worse? In fact, yes it could have; we were spared a 120 year copyright term for corporate works, as earlier drafts foreshadowed. In the end corporate works are to be protected for 70 years after publication or performance, or if they are not published within 25 years after they were created, for 70 years after their creation. This could make a big difference in practice. It means that the film Casablanca, probably protected in the United States until 2038, would already be in the public domain in other TPP countries, even under a life plus 70 year copyright term.
New to the latest text are the transition periods in Section J, which allow some countries a longer period for complying with some of their obligations, including copyright term. For example, Malaysia has been allowed two years to extend its copyright term to life plus 70 years. For Vietnam, the transition period is five years. New Zealand is the country receiving the most “generous” allowance; its term will increase to life plus 60 years initially, rising to the full life plus 70 year term within eight years. Yet Canada, on the other hand, has not been given any transition period at all.
Ban on Circumventing Digital Rights Management (DRM)
The provisions in QQ.G.10 that prohibit the circumvention of DRM or the supply of devices for doing so are little changed from earlier drafts, other than that the opposition of some countries to the most onerous provisions of those drafts was evidently to no avail. For example, Chile earlier opposed the provision that the offense of DRM circumvention is to be “independent of any infringement that might occur under the Party’s law on copyright and related rights,” yet the final text includes just that requirement.
The odd effect of this is that someone tinkering with a file or device that contains a copyrighted work can be made liable (criminally so, if wilfullness and a commercial motive can be shown), for doing so even when no copyright infringement is committed. Although the TPP text does allow countries to pass exceptions that allow DRM circumvention for non-infringing uses, such exceptions are not mandatory, as they ought to be.
The parties’ flexibility to allow DRM circumvention also requires them to consider whether rightsholders have already taken measures to allow those non-infringing uses to be made. This might mean that rightsholders will rely on the walled-garden sharing capabilities built in to their DRM systems, such as Ultraviolet, to oppose users being granted broader rights to circumvent DRM.
Alongside the prohibition on circumvention of DRM is a similar prohibition (QQ.G.13) on the removal of rights management information, with equivalent civil and criminal penalties. Since this offense is, once again, independent of the infringement of copyright, it could implicate a user who crops out an identifying watermark from an image, even if they are using that image for fair use purposes and even if they otherwise provide attribution of the original author by some other means.
The distribution of devices for decrypting encrypted satellite and cable signals is also separately proscribed (QQ.H.9), posing a further hazard to hackers wishing to experiment with or to repurpose broadcast media.
Criminal Enforcement and Civil Damages
On damages, the text (QQ.H.4) remains as bad as ever: rightsholders can submit “any legitimate measure of value” to a judicial authority for determination of damages, including the suggested retail price of infringing goods. Additionally, judges must have the power to order pre-established damages (at the rightsholder’s election), or additional damages, each of which may go beyond compensating the rightsholder for its actual loss, and thereby create a disproportionate chilling effect for users and innovators.
No exception to these damages provisions is made in cases where the rightsholder cannot be found after a diligent search, which puts the kibosh on ideas for the introduction of an orphan works regime that would cap remedies available against those who reproduce these otherwise-unavailable works.
One of the scariest parts of the TPP is that not only can you be made liable to fines and criminal penalties, but that any materials and implements used in the creation of infringing copies can also be destroyed (QQ.H.4(12)). The same applies to devices and products used for circumventing DRM or removing rights management information (QQ.H.4(17)). Because multi-use devices such as computers are used for a diverse range of purposes, this is once again a disproportionate penalty. This could lead to a family’s home computer becoming seized simply because of its use in sharing files online, or for ripping Blu-Ray movies to a media center.
In some cases (QQ.H.7), the penalties for copyright infringement can even include jail time. Traditionally, this has because the infringer is operating a business of commercial piracy. But under the TPP, any act of willful copyright infringement on a commercial scale renders the infringer liable to criminal penalties, even if they were not carried out for financial gain, provided that they have a substantial prejudicial impact on the rightsholder. The copying of films that are still playing in movie theaters is also subject to separate criminal penalties, regardless of the scale of the infringement.
Trade Secrets
The severity of the earlier language on trade secrets protection has not been abated in the final text. It continues to criminalize those who gain “unauthorized, willful access to a trade secret held in a computer system,” without any mandatory exception for cases where the information is accessed or disclosed in the public interest, such as by investigative journalists or whistleblowers.
There is no evident explanation for the differential treatment given to trade secrets accessed or misappropriated by means of a computer system, as opposed to by other means; but it is no surprise to find the U.S. pushing such a technophobic provision, which mirrors equivalent provisions of U.S. law that have been used to persecute hackers for offenses that would otherwise have been considered much more minor.
Top-Down Control of the Internet
ICANN, the global domain name authority, provoked a furore earlier this year over proposals that could limit the ability for owners of domain names to shield their personal information from copyright and trademark trolls, identity thieves, scammers and harassers.
The TPP has just ridden roughshod over that entire debate (at least for country-code top-level domains such as .us, .au and .jp), by cementing in place rules (QQ.C.12) that countries must provide “online public access to a reliable and accurate database of contact information concerning domain-name registrants.”
The same provision also requires countries to adopt an equivalent to ICANN’s flawed Uniform Domain-Name Dispute Resolution Policy (UDRP), despite the fact that this controversial policy is overdue for a formal review by ICANN, which might result in the significant revision of this policy. Where would this leave the TPP countries, that are locked in to upholding a UDRP-like policy for their own domains for the indefinite future?
The TPP’s prescription of rules for domain names completely disregards the fact that most country code domain registries have their own, open, community-driven processes for determining rules for managing domain name disputes. More than that, this top-down rulemaking on domain names is in direct contravention of the U.S. administration’s own firmly-stated commitment to uphold the multi-stakeholder model of Internet governance. Obviously, Internet users cannot trust the administration that it means what it says when it gives lip-service to multi-stakeholder governance—and that has ramifications that go even even deeper than this terrible TPP deal.
ISP Liability
The provisions on ISP liability (Appendix Section I), as we previously found in the last leaked text, are not quite as permissive as we hoped. It will still require most countries to adopt a version of the flawed U.S. DMCA notice-and-takedown system, albeit with a few safeguards such as penalties for those who issue wrongful takedown notices, and allowing (but not requiring) a Japanese-style system of verification of takedown notices by an independent body of ISPs and rightsholders.
It is true that Canada’s notice-and-notice regime is also allowed, but effectively only for Canada—no other country that did not have an equivalent system as of the date of the agreement is allowed to benefit from that flexibility. Even in Canada’s case, this largesse is only afforded because of the other enforcement measures that rightsholders enjoy there—such as a tough regime of secondary liability for authorization of copyright infringement.
Similarly Chile’s system under which ISPs are not required to take down content without a judicial order is explicitly grandfathered in, but no other country joining the TPP in the future will be allowed to have a similar system.
In addition, although there is no explicit requirement for a graduated response regime of copyright penalties against users, ISPs are still roped in as copyright enforcers with the vague requirement (Appendix Section 1) that they be given “legal incentives…to cooperate with copyright owners to deter the unauthorized storage and transmission of copyrighted materials or, in the alternative, to take other action to deter the unauthorized storage and transmission of copyright materials”.
Good Points?
Quite honestly there are no parts of this agreement that are positively good for users. Of course, that doesn’t mean that it’s not improved over the earlier, horrendous demands of the U.S. negotiators. Some of the areas in which countries rightly pushed back against the U.S., and which are reflected in the final text are:
- The exhaustion of rights provision (QQ.A.11) that upholds the first sale doctrine of U.S. law, preventing copyright owners from extending their control over the resale of copyright works once they have first been placed in the market. In particular, this makes parallel importation of cheaper versions of copyright works lawful—and complementing this is an explicit authorization of devices that bypass region-coding on physical copies of such works (QQ.G.10, though this does not extend to bypassing geoblocking of streaming services).
- A thoroughly-misguided provision that would have extended copyright protection to temporary or “buffer” copies in a computer system was one of the earliest rightsholder demands dropped by the USTR, and rightfully so, given the damage this would have wreaked to tech companies and users alike.
But we have struggled to come up with more than two positive points about the TPP, and even then the absence of these tragic mistakes is a pretty poor example of a positive point. If you look for provisions in the TPP that actually afford new benefits to users, rather than to large, rights-holding corporations, you will look in vain. The TPP is the archetype of an agreement that exists only for the benefit of the entitled, politically powerfully lobbyists who have pushed it through to completion over the last eight years.
There is nothing in here for users and innovators to support, and much for us to fear—the ratcheting up of the copyright term across the Pacific rim, the punitive sanctions for DRM circumvention, and the full frontal attack on hackers and journalists in the trade secrets provision, just to mention three. This latest leak has confirmed our greatest fears—and strengthened our resolve to kill this agreement for good once it reaches Congress.
Source: globalresearch.ca